In this blog post, I will show you how to use a script I created to bypass some of IOSSecuritySuite’s features.
IOSSecuritySuite is a common library used perform anti-tampering and increase the security of an IOS application.
I’ve created a simple APP to test the IOSSecuritySuite functionalities. You can download the IPA file here.
To install it just unzip the IPA file and move the .app folder to /Applications on devices with a Rootfull jailbreak or /var/jb/Applcations on devices with Rootless jailbreak. After it, just run uicache -ar command and the app will show on homescreen. This is a print of the app running on my device. Basically it shows some features that are triggered.

The script
This is the script that I created. It will be progressively enhanced as time goes by. Download the most recent version from github.
function hook_by_export(module_name, func_name){
var target_ptr = Module.findExportByName(module_name, func_name);
if(target_ptr != null){
Interceptor.attach(target_ptr, {
onEnter: function(args){
console.log("[+] Bypassing: " + func_name)
},
onLeave: function(retval) {
retval.replace(0x0); // Force return value to be 0x0
}
});
}else{
console.log("[-] Not found: " + func_name);
}
}
setTimeout(function(){
try{
var moduleName = "Test_IOSSECURITY"; //Change it
var amIJailBroken = "$s16IOSSecuritySuiteAAC13amIJailbrokenSbyFZ";
var amIReverseengineered = "$s16IOSSecuritySuiteAAC20amIReverseEngineeredSbyFZ";
var amIProxied = "$s16IOSSecuritySuiteAAC10amIProxiedSbyFZ"
var amIDebugged = "$s16IOSSecuritySuiteAAC11amIDebuggedSbyFZ"
var isRunningEmulator = "$s16IOSSecuritySuiteAAC16amIRunInEmulatorSbyFZ"
var amITampered = "$s16IOSSecuritySuiteAAC11amITamperedySb6result_SayAA18FileIntegrityCheckOG9hitCheckstAGFZ";
var denyDebbuger = "$s16IOSSecuritySuiteAAC12denyDebuggeryyFZ";
hook_by_export(moduleName, amIJailBroken);
hook_by_export(moduleName, amIReverseengineered);
hook_by_export(moduleName, amIProxied);
hook_by_export(moduleName, amIDebugged);
hook_by_export(moduleName, isRunningEmulator);
hook_by_export(moduleName, amITampered);
hook_by_export(moduleName, denyDebbuger);
}catch(e){
console.log(e.emssage)
}
}, 1);To use this script, you need to first enumerate the module from which IOSSecuritySuite functions are called. To do it, you can follow these steps:
1 – Start your app using frida, like frida -U -f <your_app>
2 – Run the following code: Process.enumerateModulesSync();
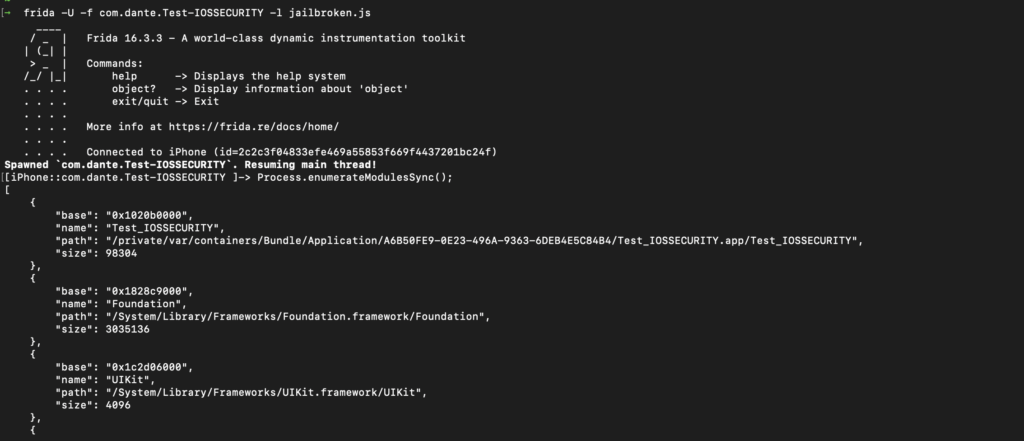
This command shows all modules currently loaded inside the application. Now you need to infer which one is the correct module. In most of cases will be something like “IOSSecuritySuite” or “SecuritySuite”. In this case is “Test_IOSSecurity”.
You need to change the variable *moduleName* inside the script by the correct module name.
Now you can just run the script as following
frida -U -f <your application> -l iossecurity.jsAll the functions are not triggered
